By default certificates are tied to the exact server name they are created for. Which is normally the FQDN of the server. If you create a certificate for the server myserver.vstrong.info and then connect to it by the short name myserver / MyServer or by any other DNS aliases, the certificate will not be seen as a trusted certificate. There is a way to get all aliases included in the certificate.
In order to create a certificate you need an application that can generate certificate request and then send it to the Certification Authority (CA) for signing.
One of the easiest application that can gererate certificate request is OpenSSL. Download and install OpenSSL from this link http://slproweb.com/products/Win32OpenSSL.html
I will be installing OpenSSL on 64-bit OS, so lets download Win64 OpenSSL v1.0.1e Light and its pre-requisite Microsoft Visual C++ 2008 Redistributible (x64).
Installation is straightforward, accept the defaults and select Copy OpenSSL DLLs to The OpenSSL binaries (/bin) directory. Please donate generously!
By default, OpenSSL looks for a configuration file in the user’s local profile directory:
C:OpenSSL-Win64bin>openssl WARNING: can't open config file: /usr/local/ssl/openssl.cnf OpenSSL> exit
Run the following SET command to specify the configuration file:
SET OPENSSL_CONF=C:OpenSSL-Win64binopenssl.cfg
Before we create any certificates, lets make a backup of the default OpenSSL configuration file and pre-configure default information that will be applicable to all certificates that we are going to create:
[ req_distinguished_name ] countryName = Country Name (2 letter code) countryName_default = UK stateOrProvinceName = State or Province Name (full name) stateOrProvinceName_default = Greater London localityName = Locality Name (eg, city) localityName_default = London 0.organizationName = Organization Name (eg, company) 0.organizationName_default = vStrong.info organizationalUnitName = Organizational Unit Name (eg, section) organizationalUnitName_default = IT
By default, OpenSSL create 1024 bit certificate request. You you need stronger certificate, you can do either of these:
- Edit openssl.cfg and amend the following line:
[ req ] default_bits = 1024
- Add this command when you run openssl:
-newkey rsa:4096
What about the aliases?
Find the [ req ] section and add/un-comment the following line:
req_extensions = v3_req
Find the [ v3_req ] section and add a new subjectAltName line and list all DNS aliases as in this example:
subjectAltName = "DNS:server001.vstrong.info, DNS:server001, DNS:SERVER001.VSTRONG.INFO, DNS:SERVER001, DNS:CITRIX, DNS:citrix, DNS:10.10.100.150"
As you can see, I added lower- and uppercase, short and FQDN server name, two aliases, ‘CITRIX’ and ‘citrix’. You can also add an IP address of the server or device. I find it quite useful as sometimes IP address is easier to remember.
Lets generate the certificate request!
Open Windows Command Prompt, navigate to the the directory where you installed OpenSSL and run the following:
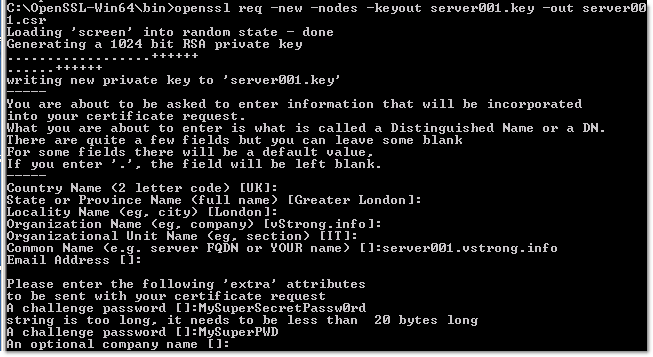
openssl req -new -nodes -keyout server001.key -out server001.csr
There will be a series of questions. Answer each question and make note of the challenge password; it will be needed later in the process.
The certificate creation process will create 2 files:
- *.crt – the CSR that will be signed by the Certificate Authority to create the final certificate
- *.key – the private key in PEM format
C:OpenSSL-Win64bin>openssl req -new -nodes -keyout server001.key -out server001.csr Loading 'screen' into random state - done Generating a 1024 bit RSA private key ..................++++++ ......++++++ writing new private key to 'server001.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [UK]: State or Province Name (full name) [Greater London]: Locality Name (eg, city) [London]: Organization Name (eg, company) [vStrong.info]: Organizational Unit Name (eg, section) [IT]: Common Name (e.g. server FQDN or YOUR name) []:server001.vstrong.info Email Address []: Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []:MySuperSecretPassw0rd string is too long, it needs to be less than 20 bytes long A challenge password []:MySuperPWD An optional company name []:
Signing the request
You must sign the request with Microsoft Active Directory Certificate Services.
- Open server001.csr with Wordpad (to preserve the formatting) and copy the contents onto the clipboard (Edit > Select all; Edit > Copy).
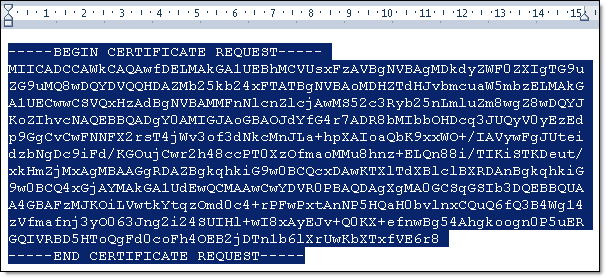
- In Internet Explorer, navigate to the Microsoft CA server.
Enter the following URL:
http://<CA_server_IP_address>/certsrv
The Certificate Services applet starts. - On the Welcome screen, below the Select a task heading, select Request a certificate.
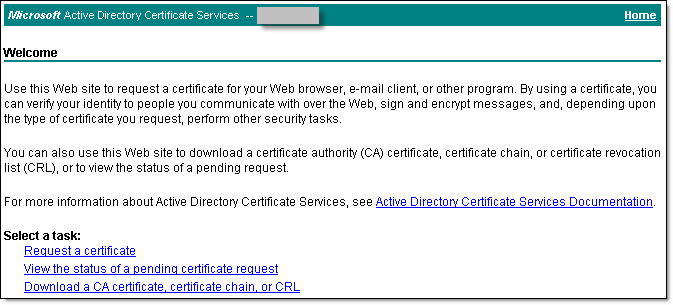
- The Request a certificate page displays. Select advanced certificate request
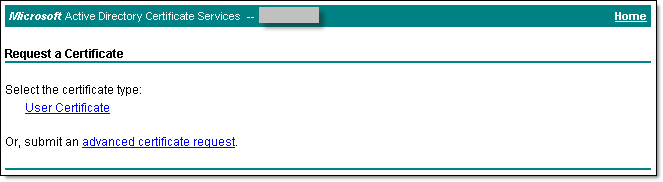
- On the Advanced Certificate Request screen, select Submit a certificate request by using a base-64-encoded CMC.
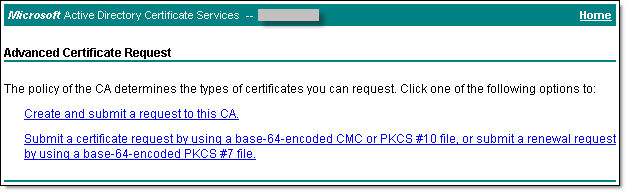
The Submit a Certificate Request or Renewal Request screen displays. - On the Submit a Certificate Request or Renewal Request screen, paste the content of the server001.csr file (previously placed on the clipboard), in the Certificate Template drop down window select Web Server or other appropriate to your needs template and click Submit.
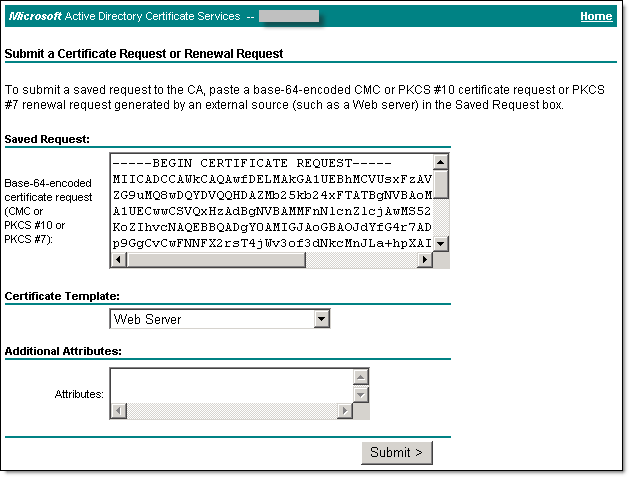
- The certificate is issued and the Certificate Issued screen displays.
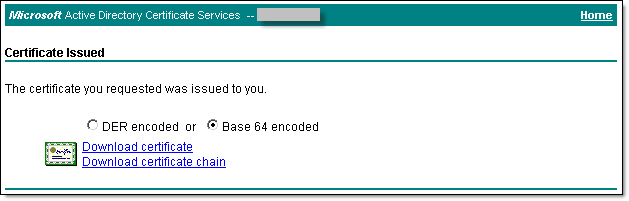
- Select the Base 64 encoded radio button and then select Download certificate. Save the certificate as server001.cer to your desktop.
- Lets confirm the certificate includes the server aliases:
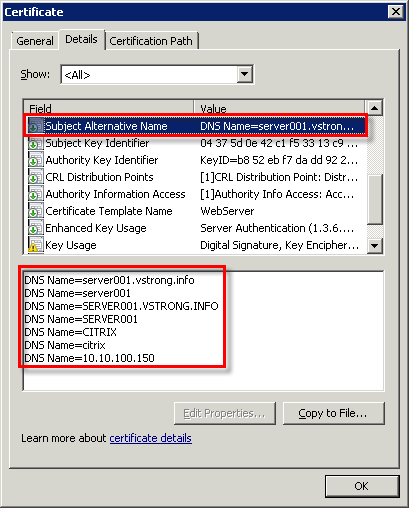
Hope this will help.

Really helpful! Thank you Mark for posting :)
Hi, if I want to do this, do I also need to create extra DNS records using the shortname and the same IP address as I used for my original FQDN DNS entry for the appliance?